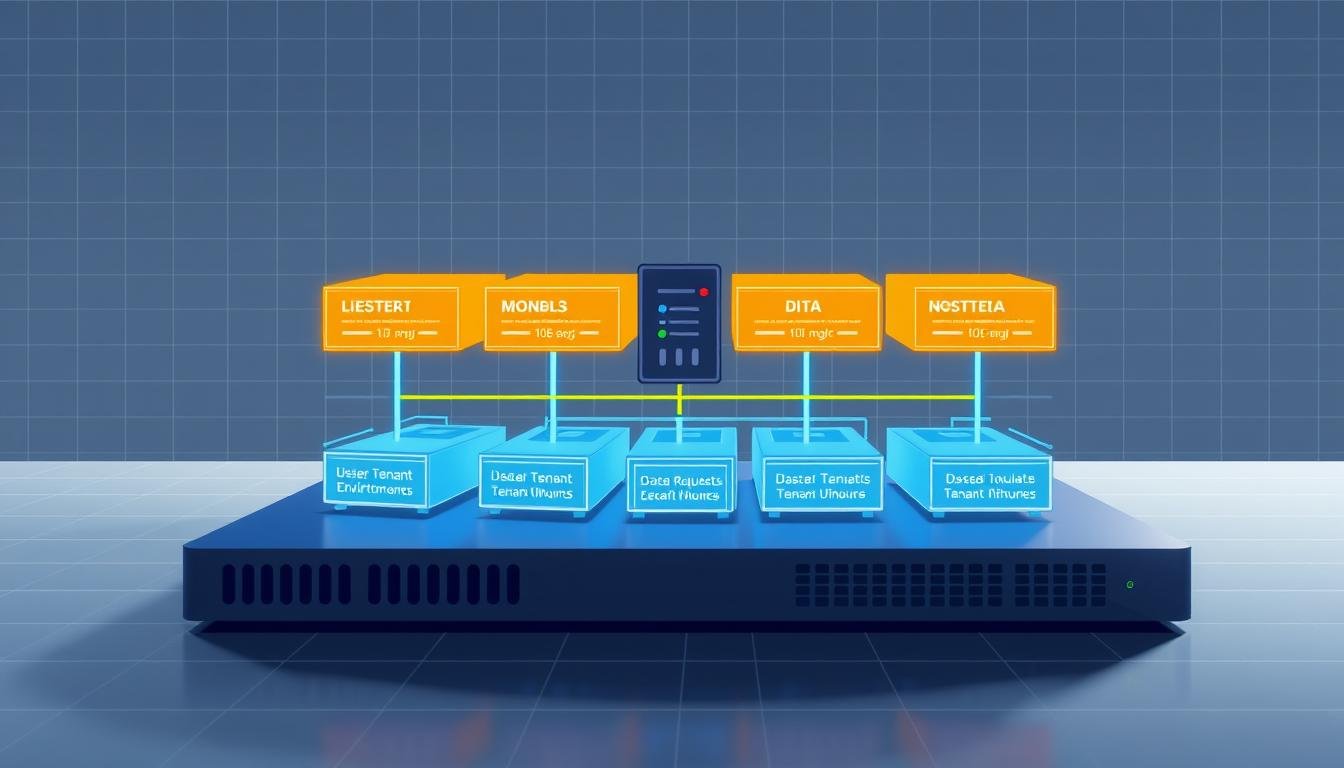
What if the key to scaling your startup’s software isn’t building more, but building smarter? Many technical leaders assume rapid growth requires endless customization for each client. But there’s a better way to balance flexibility with efficiency.

Modern cloud-based solutions thrive on shared infrastructure that serves multiple customers securely. This approach lets businesses customize workflows, user permissions, and even database structures – all while maintaining a single codebase. For startups, this isn’t just convenient. It’s often the difference between scalable success and operational gridlock.
Choosing the right foundation impacts everything from development costs to how quickly you adapt to market changes. While single-client systems feel safer initially, they create silos that strain resources as you grow. The alternative? A unified design that isolates customer data while maximizing hardware and software investments.
Key Takeaways
- Shared infrastructure reduces costs while maintaining security between clients
- Customizable workflows and permissions without code changes
- Scalable data management through logical separation
- Cloud-native designs enable faster updates and feature rollouts
- Strategic architecture choices directly impact long-term growth potential
Introducing Multi-Tenant SaaS Architecture
Imagine an office building where every company has private floors but shares elevators and security systems. This real-world analogy helps explain how modern software can serve multiple groups securely. Shared systems let organizations customize experiences while keeping data separate – a critical balance for growing businesses.

Core Concepts and Terminology
At its heart, this approach lets distinct user groups operate within one system. We call these groups tenants – they could be departments, clients, or partner organizations. Each gets dedicated storage and processing space through logical partitions, like digital vaults within a shared bank.
Resource sharing goes beyond physical servers. Cloud platforms enable this separation through software-defined boundaries. Tenants access common features like authentication protocols, but their configurations and user permissions stay unique. This setup reduces hardware costs by 40-60% compared to individual systems.
Understanding Tenant Isolation
Isolation mechanisms act like soundproof walls between hotel rooms. Data encryption and access controls prevent unauthorized cross-tenant interactions. Our team implements role-based policies that automatically segment information, ensuring marketing teams never see engineering data unless explicitly permitted.
This logical separation allows updates to roll out simultaneously across all groups. When we enhanced a client’s reporting tools last quarter, 85+ tenant environments received the upgrade without manual interventions. The system scales effortlessly because resources expand beneath a stable interface layer.
Comparing Multi-Tenant and Single-Tenant Architectures
What separates thriving platforms from those buckling under growth? Often, it’s the choice between isolated systems and shared solutions. Startups face critical decisions when balancing customization needs with operational efficiency.

Advantages of Pooled Resources
Shared infrastructure slashes costs while maintaining performance. By pooling servers and databases, teams reduce hardware expenses by 50-70% compared to single-client systems. Updates deploy simultaneously across all users, eliminating version conflicts.
This approach simplifies scaling. Adding new tenants requires no additional hardware – existing resources expand logically. One e-commerce client scaled from 12 to 300+ stores without infrastructure changes, maintaining 99.9% uptime.
Balancing Flexibility and Control
Single-tenant architecture offers complete isolation – ideal for strict compliance needs. Financial institutions often choose this model for dedicated encryption layers. However, maintenance costs typically run 3x higher than shared systems.
Multi-tenant designs prioritize efficiency over granular control. While tenants customize dashboards and workflows, core system modifications require provider approval. This trade-off enables rapid iteration – features reach all users faster through centralized development.
Security remains robust through logical separation. Role-based access and encrypted data partitions prevent cross-tenant leaks, though physical isolation provides marginally stronger protection. Most growing businesses find shared systems strike the right balance between safety and agility.
Economic Benefits and Cost Efficiency in SaaS Models
Cost efficiency isn’t about cutting corners—it’s about smart allocation. Shared operational models let businesses reinvest savings into innovation rather than redundant systems. By distributing expenses across multiple groups, providers deliver enterprise-level tools at startup-friendly prices.
Leveraging Shared Resources
Pooled infrastructure slashes upfront and ongoing expenses. One cloud instance can securely handle hundreds of clients, with costs divided proportionally. This approach reduces hardware needs by 60%+ compared to isolated setups. Providers reinvest these savings into faster updates and enhanced security protocols.
Subscription pricing thrives under this model. Predictable monthly fees replace unpredictable capital expenditures. A recent study showed companies using shared systems cut annual IT costs by 42% while improving service reliability. Clients gain access to premium tools without bearing full maintenance burdens.
Dedicated systems drain budgets through duplicated efforts. Shared environments eliminate redundant servers, cooling systems, and energy consumption. One logistics platform reduced its carbon footprint by 35% after migrating to a resource-sharing model—proof that efficiency benefits both wallets and ecosystems.
Startups particularly benefit from this economic structure. They gain scalable infrastructure without massive upfront investments. Providers maintain healthy margins by optimizing resource usage, creating pricing flexibility that attracts diverse customers. It’s a sustainable cycle where growth fuels affordability.
Achieving Scalability and Performance in Cloud Environments
Scaling cloud-based platforms requires more than just adding servers—it demands intelligent resource management. Shared environments let tenants expand user bases instantly, with new accounts activating in minutes rather than weeks. This agility comes from unified software instances that eliminate hardware provisioning delays.
One logistics client grew from 150 to 2,000+ users in six months without infrastructure changes. Their subscription model allowed seamless scaling—every new tenant accessed the same optimized instance. “The cloud’s elasticity lets businesses pivot faster than ever,” notes AWS Solutions Architect Michael Chen. “But without guardrails, shared resources become liabilities.”
Strategies to Handle Noisy Neighbors
Resource competition poses the biggest risk in shared environments. When one tenant’s spike in API calls slows others’ applications, performance suffers system-wide. We combat this through:
- Dynamic quotas: Automatic limits on CPU usage and database queries
- Priority-based routing: Critical workflows get dedicated bandwidth
- Real-time analytics: Instant alerts for abnormal usage patterns
Auto-scaling tools add computing power during traffic surges, while load balancers distribute requests evenly. These measures maintain 99.95% uptime across tenant groups—even during Black Friday sales spikes.
Effective monitoring separates functional platforms from unstable ones. Our team uses distributed tracing to pinpoint bottlenecks before users notice delays. By combining cloud-native tools with custom thresholds, we ensure fair resource allocation without compromising flexibility.
Security and Data Isolation Strategies for Tenant Protection
How do you protect sensitive information when multiple groups share the same digital space? Shared environments demand airtight safeguards to prevent cross-tenant vulnerabilities. Our team prioritizes three pillars: granular permissions, encrypted boundaries, and proactive monitoring.
Locking Down Access Points
Robust authentication systems form the first defense layer. We implement role-based policies that tie permissions to job functions. For example, HR teams see employee records but can’t access financial databases. Multi-factor authentication adds extra verification steps for high-risk actions like exporting files.
Access logs track every interaction with sensitive data. Automated alerts flag unusual patterns—like a user downloading 500 files in 10 minutes. These controls reduce internal threats while maintaining workflow efficiency.
Building Encrypted Barriers
Data encryption transforms information into unreadable code during storage and transmission. Even if breached, stolen files remain useless without decryption keys. We use AES-256 encryption for databases and TLS 1.3 for data in motion.
| Security Measure | Protection Scope | Implementation |
|---|---|---|
| Field-Level Encryption | Individual data columns | Credit cards, SSNs |
| Tokenization | Sensitive text replacement | Payment processing |
| DLP Scanning | File transfers & downloads | Block personal device saves |
Data Loss Prevention (DLP) tools act as digital bouncers. They block unauthorized file shares and monitor cloud storage for policy violations. When a user tries emailing client records externally, the system either quarantines the message or requires manager approval.
Regular audits ensure compliance with GDPR and CCPA standards. Independent reviews verify that isolation mechanisms function as intended—because trust requires proof, not promises.
Customization and Tenant-Specific Configurations
Tailoring software to diverse needs often feels like walking a tightrope. Push too far toward rigidity, and users revolt. Lean into endless customization, and updates become nightmares. Modern platforms solve this through controlled adaptability – letting businesses shape tools without touching core code.
Adapting Application Settings Without Coding
Leading solutions offer configuration layers that sit above the core software. Users modify workflows through drag-and-drop interfaces rather than command lines. A retail client recently redesigned their inventory dashboard in 23 minutes – no developers involved.
Key customizable elements include:
- User role permissions and access tiers
- Data field labels and reporting formats
- Approval chains for critical processes
These changes apply only to individual tenant environments. When we update the core application, customizations stay intact through abstraction layers. It’s like remodeling office furniture without altering the building’s foundation.
Balancing Standardization with Flexibility
Effective systems provide guardrails, not handcuffs. Preset configuration options prevent destabilizing changes while allowing meaningful adjustments. Our team implements:
| Customization Level | Tenant Control | System Impact |
|---|---|---|
| UI Themes | Full | None |
| Workflow Rules | Partial | Low |
| Data Models | Approved Templates | Medium |
This structured approach maintains upgrade compatibility. When we launched new API integrations last quarter, 97% of tenant configurations required zero adjustments. Businesses keep their unique setups while benefiting from system-wide improvements.
Configuration management tools track all changes, enabling rollbacks if needed. Audit trails show who modified settings and when – crucial for compliance-driven industries. By combining flexibility with oversight, platforms support innovation without sacrificing stability.
Managing User Identities and Access Controls
Secure access management forms the backbone of trusted software ecosystems. We implement layered controls that verify identities while preserving workflow efficiency. Every interaction begins with answering two questions: “Who are you?” and “What can you access?”
Integrating Single Sign-On Solutions
Modern teams refuse to memorize dozens of passwords. Our SSO integrations let employees use existing organizational credentials across applications. Microsoft Azure AD and Okta deployments reduce login friction by 78% while maintaining security audits.
This approach eliminates duplicate accounts and password resets. When users leave an organization, access revocation happens instantly across all connected systems. We configure conditional policies that require extra verification for sensitive actions like exporting financial data.
Defining Role-Based Permissions
Granular controls put customers in the driver’s seat. Tenant administrators assign roles like “Invoice Approver” or “Project Viewer” through intuitive dashboards. These permissions automatically apply across departments, locations, and third-party integrations.
Key components of our permission framework:
- Context-aware authorization: Checks user roles AND tenant membership
- Time-bound access: Temporary privileges for contractors
- Audit trails: Tracks permission changes and access attempts
One healthcare client reduced unauthorized data access by 92% after implementing tiered roles. Their compliance team now creates custom permission sets for different care teams without developer involvement. This balance of power and simplicity defines modern access management.
Architectural Models for Multi-Tenant Saa
The foundation you choose today shapes tomorrow’s growth trajectory. We’ve seen startups accelerate expansion by 300%+ using shared-resource designs that balance customization with operational efficiency. The right model acts as an invisible growth engine—scaling silently while teams focus on innovation.
Three approaches dominate modern implementations. Database-per-tenant setups offer strict isolation for compliance-heavy industries. Shared-table designs maximize hardware efficiency through logical partitioning. Hybrid models blend both strategies, adapting to evolving business needs.
Success lies in matching patterns to use cases. E-commerce platforms thrive with resource pooling, while healthcare systems often require dedicated storage layers. Our team implements dynamic frameworks that let clients adjust isolation levels as regulations or customer demands shift.
Cloud-native tools now simplify these decisions. Automated scaling and built-in encryption let technical leaders prioritize feature development over infrastructure tuning. The result? Faster time-to-market and updates that deploy across all tenants simultaneously.
Your architecture shouldn’t just solve current challenges—it must unlock future opportunities. By combining proven models with modern cloud capabilities, businesses build adaptable systems that grow as boldly as their ambitions.